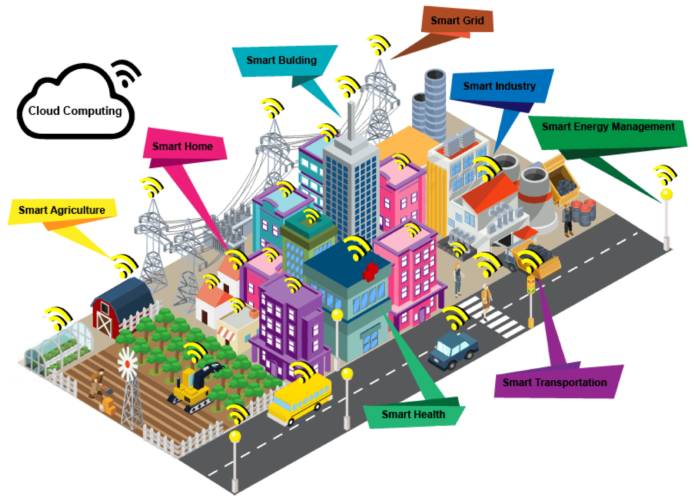
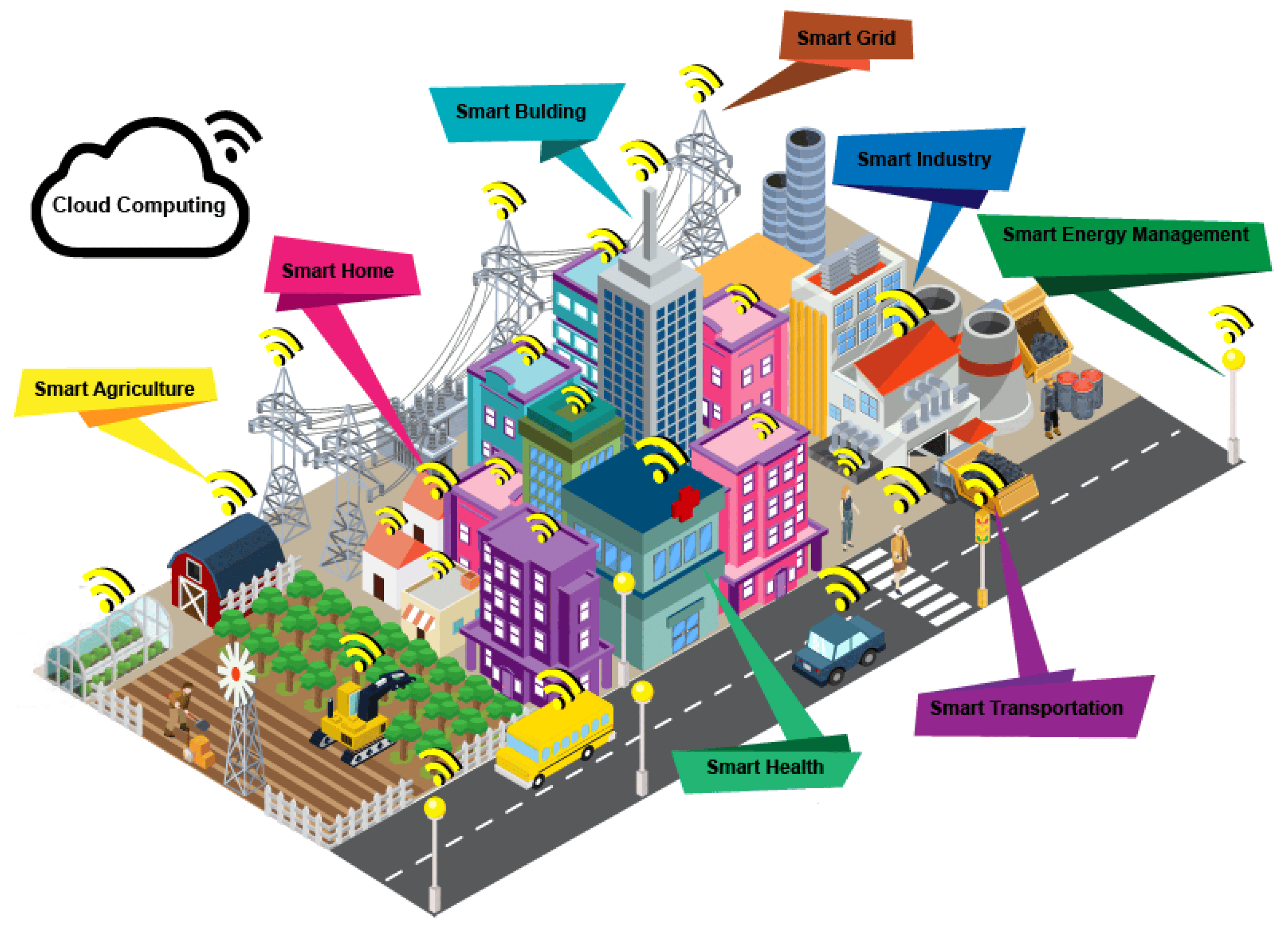
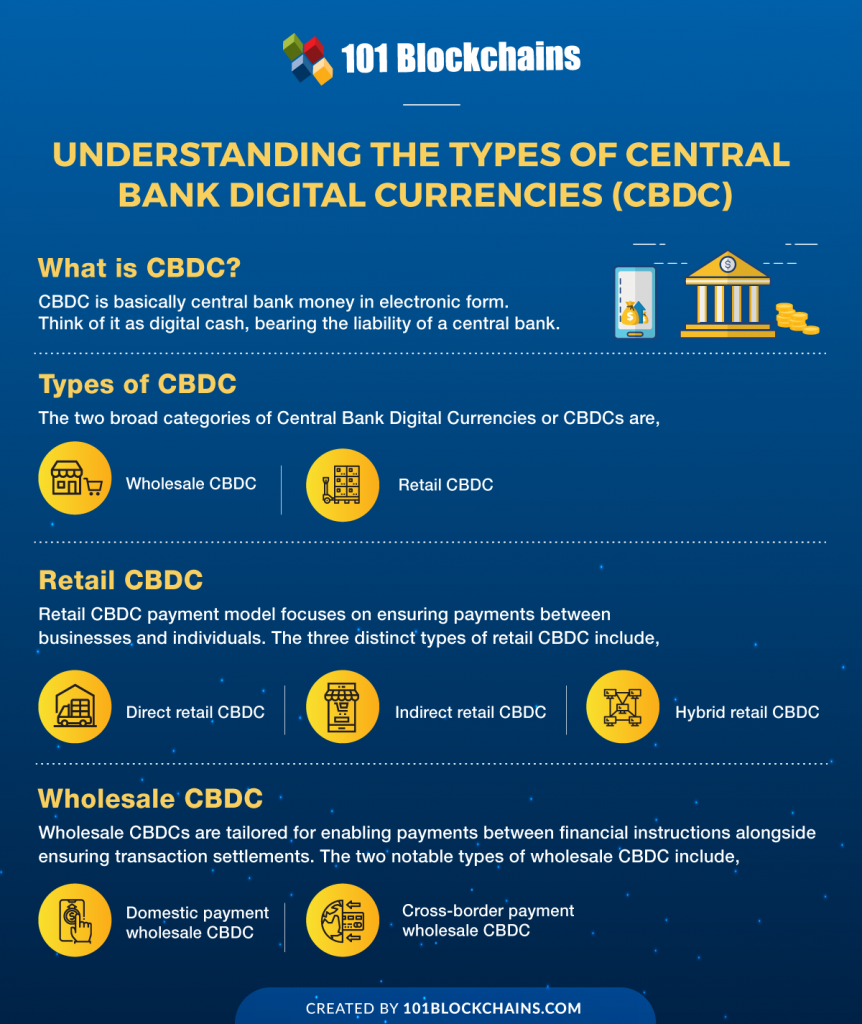
In recent years, the integration of Artificial Intelligence (AI) into healthcare has transformed patient care dramatically. From predictive analytics to robotic surgeries, AI has proven its potential in improving outcomes, enhancing efficiency, and reducing costs. However, as healthcare becomes increasingly digitized, the importance of human empathy in patient care cannot be overlooked. Balancing AI technology with human touch is crucial for delivering comprehensive and compassionate healthcare services.
The Rise of AI in Healthcare
Enhancements in Diagnostics
AI technology is now capable of analyzing vast amounts of data faster and more accurately than human practitioners. For instance, machine learning algorithms can sift through thousands of medical images to detect anomalies such as tumors or fractures that might be missed by the human eye. This capability not only improves diagnostic accuracy but also speeds up the time to treatment, which is critical in many medical situations.
Streamlining Administrative Tasks
AI can automate many administrative tasks that typically burden healthcare professionals, such as appointment scheduling, billing, and patient record management. This automation frees up valuable time for healthcare workers to focus more on patient interaction and care rather than paperwork. As a result, healthcare providers can spend more quality time with their patients, fostering better relationships and understanding their needs.
Personalized Treatment Plans
AI’s ability to analyze patient data allows for personalized treatment plans. By assessing a patient’s medical history, genetics, and lifestyle factors, AI can recommend tailored interventions that are more effective than one-size-fits-all approaches. This level of customization enhances patient satisfaction and can lead to better health outcomes.
The Critical Role of Empathy in Patient Care
While AI can offer remarkable advantages, the human aspect of healthcare—empathy—remains irreplaceable. Empathy involves understanding and sharing the feelings of others, a crucial component in patient care that significantly impacts patient outcomes.
Building Trust and Rapport
Empathy fosters trust between healthcare providers and patients. When healthcare professionals demonstrate genuine concern and understanding, patients are more likely to communicate openly about their symptoms and concerns. This transparency is essential for accurate diagnoses and effective treatment plans. A 2016 study published in Health Affairs found that patients who felt understood by their doctors were more likely to adhere to treatment plans and report better health outcomes.
Improving Patient Experience
Healthcare is not just about treating illnesses; it is also about providing a positive experience for patients. Empathetic care contributes to a supportive environment where patients feel valued and cared for. This experience can alleviate anxiety, enhance patient satisfaction, and promote healing. According to a study by the Berkshire Healthcare Foundation, patients who felt their healthcare providers were empathetic were more satisfied with their overall care experience.
Emotional Support
Many patients face significant emotional challenges during their healthcare journeys, such as fear of diagnosis, treatment side effects, or financial burdens. Healthcare professionals who offer empathy can provide emotional support, helping patients navigate these challenges. This support is vital for mental well-being and can lead to better adherence to treatment regimens.
The Balance Between AI and Empathy
Complementary Roles
Rather than viewing AI and empathy as opposing forces, healthcare professionals should see them as complementary elements that, when balanced, enhance patient care. AI can manage data and analytics, while human practitioners can focus on understanding patients’ emotional and psychological needs.
Training Healthcare Professionals
Integrating AI into healthcare does not mean that empathy should be sidelined. Healthcare professionals must receive training not only in technology but also in emotional intelligence. Courses on communication skills, active listening, and emotional support can equip practitioners to use AI effectively while maintaining a strong human connection with patients.
Utilizing AI to Enhance Empathy
Interestingly, AI can also be used to enhance empathy in healthcare. For instance, virtual reality (VR) applications can simulate patient experiences, allowing healthcare providers to better understand the challenges and emotions their patients face. By putting themselves in their patients’ shoes, providers can develop greater empathy and improve their care approach.
Patient-Centric AI Applications
Moreover, AI applications can be designed with a patient-centric focus, prioritizing the human aspect. For example, AI chatbots can provide patients with 24/7 access to information and support, but they can also be programmed to encourage empathy in their interactions. By using natural language processing, these chatbots can respond to patients in a caring manner, thus bridging the gap between technology and human touch.
Challenges in Balancing AI and Empathy
Over-Reliance on Technology
One of the challenges of integrating AI into healthcare is the risk of over-reliance on technology. Healthcare professionals may be tempted to depend solely on AI for decision-making, potentially diminishing the human aspect of care. This scenario could lead to a lack of emotional connection and understanding, which are vital for effective patient-provider relationships.
Data Privacy Concerns
The use of AI in healthcare also raises concerns about data privacy and security. Patients must trust that their personal health information is handled with the utmost confidentiality. Healthcare providers must navigate these concerns while ensuring that the technology they use does not compromise patient trust.
Resistance to Change
Another challenge is the resistance to adopting new technologies among healthcare professionals. Many practitioners may feel overwhelmed by the rapid pace of technological advancements and may hesitate to integrate AI into their practice. Addressing these concerns through adequate training and support is essential for a smooth transition.
The Future of Patient Care: A Harmonious Blend
As we move forward, the future of patient care will likely be defined by a harmonious blend of AI and empathy. Healthcare providers who embrace this dual approach will be better positioned to meet the needs of their patients and deliver high-quality care.
Advocating for a Holistic Approach
Healthcare institutions should advocate for a holistic approach that values both technology and human connection. By prioritizing patient-centered care that combines AI’s efficiency with the compassion of healthcare providers, we can create a more effective and empathetic healthcare system.
Research and Development
Investment in research and development is crucial to explore new ways to integrate AI into healthcare without sacrificing empathy. Innovations that facilitate better communication, enhance emotional understanding, and maintain patient trust will be vital.
Policy and Regulation
Policymakers must also play a role in shaping the future of AI in healthcare. Regulations should promote the ethical use of AI, ensuring that patient privacy is protected while fostering innovation that enhances patient care. Collaborative efforts between technologists, healthcare providers, and policymakers will be essential in creating a balanced system.
Conclusion
In conclusion, while AI offers tremendous potential for enhancing patient care, it is essential to recognize the irreplaceable value of human empathy. Balancing these two elements will not only improve patient outcomes but also enrich the healthcare experience. By training healthcare professionals to harness the power of AI while fostering empathy, we can create a healthcare landscape that prioritizes both innovation and compassion. The human touch, combined with advanced technology, i







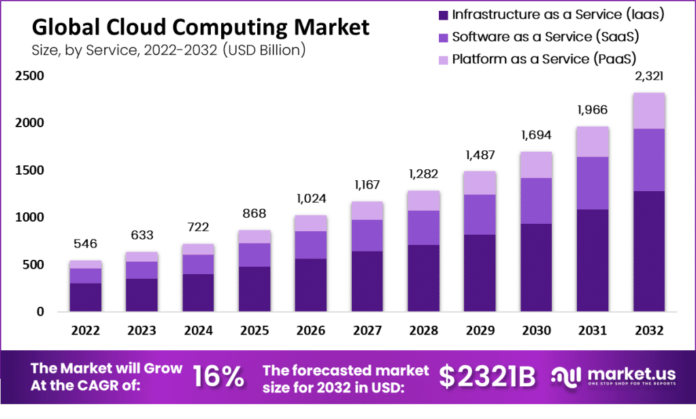

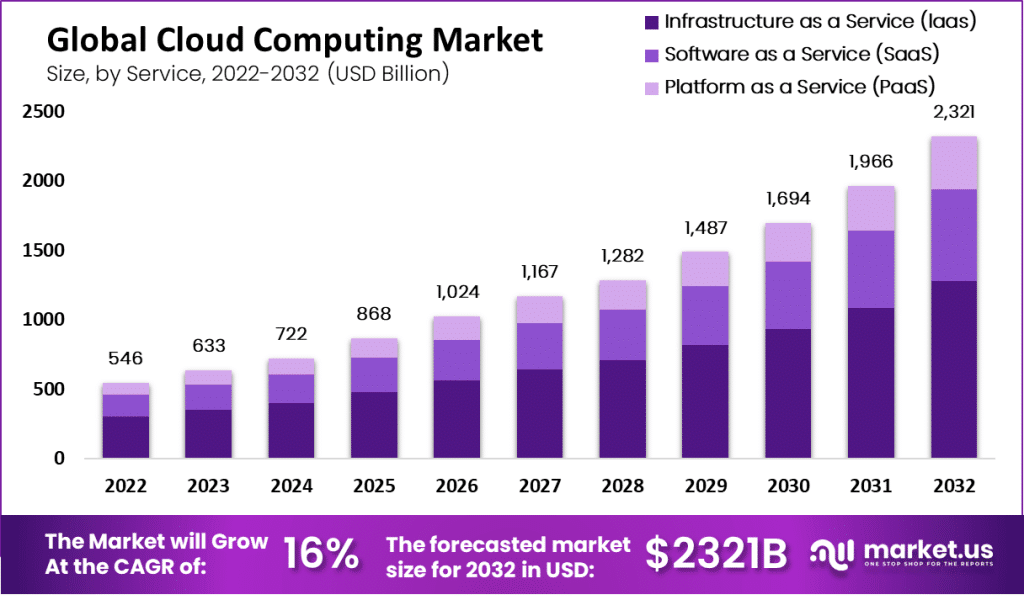
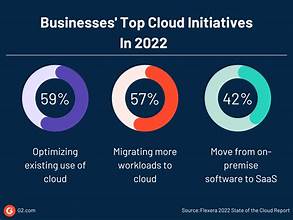























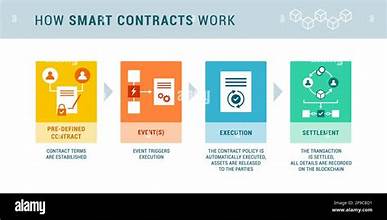
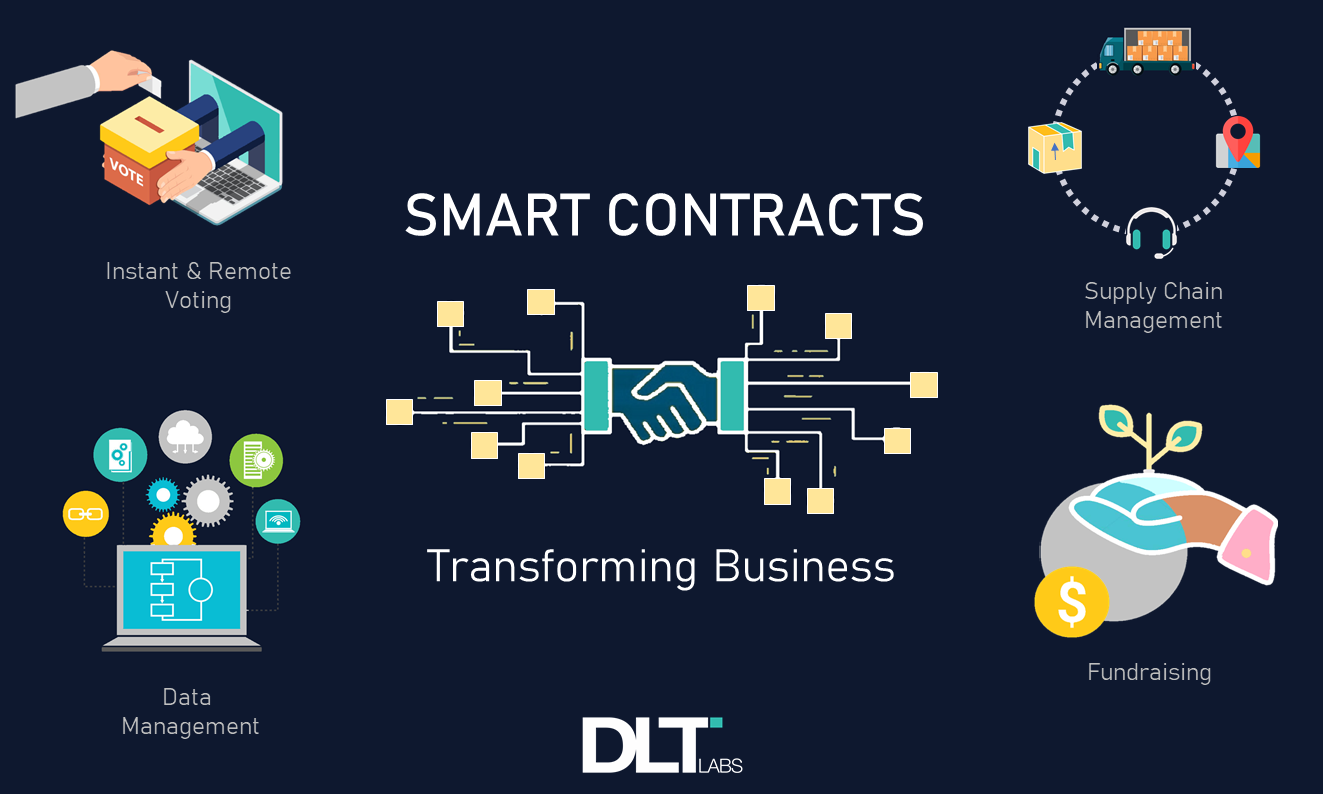







































 apidly evolving world of finance, Decentralized Finance (DeFi) has emerged as a groundbreaking trend. As we navigate through 2024, it’s crucial to understand the current state of DeFi, key trends, and future predictions. This article delves into the latest developments in DeFi, offering insights into its trajectory and potential impact on the financial landscape.
apidly evolving world of finance, Decentralized Finance (DeFi) has emerged as a groundbreaking trend. As we navigate through 2024, it’s crucial to understand the current state of DeFi, key trends, and future predictions. This article delves into the latest developments in DeFi, offering insights into its trajectory and potential impact on the financial landscape.