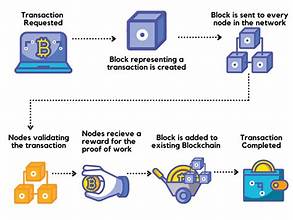
Blockchain technology has revolutionized various sectors by offering secure, transparent, and decentralized solutions. However, as blockchain continues to gain prominence, security threats have become increasingly sophisticated. In 2024, addressing these threats is crucial for ensuring the integrity and reliability of blockchain systems. This article explores the top blockchain security threats and provides actionable strategies for mitigating them.
1. Smart Contract Vulnerabilities
What They Are:
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. While they automate processes and reduce human error, they are also susceptible to bugs and vulnerabilities. Common issues include reentrancy attacks, integer overflows, and unhandled exceptions.
Mitigation Strategies:
- Code Audits: Regularly perform comprehensive audits using automated tools and manual reviews by experienced auditors.
- Testing: Implement rigorous testing procedures, including unit tests, integration tests, and formal verification.
- Upgradable Contracts: Design contracts to be upgradable so that vulnerabilities can be patched without losing data.
2. 51% Attacks
What They Are:
A 51% attack occurs when a single entity controls over 50% of a blockchain network’s mining or validating power. This can lead to double-spending, transaction reversal, and network disruptions.
Mitigation Strategies:
- Decentralization: Promote decentralization in mining and validation processes to reduce the risk of any single entity gaining majority control.
- Proof-of-Stake: Consider using Proof-of-Stake (PoS) consensus mechanisms, which are less vulnerable to 51% attacks compared to Proof-of-Work (PoW).
3. Phishing and Social Engineering
What They Are:
Phishing attacks involve deceiving individuals into revealing their private keys or sensitive information through fraudulent means. Social engineering manipulates individuals into divulging confidential data.
Mitigation Strategies:
- Education: Educate users about common phishing tactics and social engineering schemes.
- Multi-Factor Authentication (MFA): Implement MFA to add an additional layer of security beyond just passwords.
- Secure Interfaces: Ensure that all user interfaces for blockchain applications are secure and free from vulnerabilities.
4. Network Layer Attacks
What They Are:
Network layer attacks, such as Distributed Denial of Service (DDoS) attacks, can overwhelm blockchain networks, causing delays or outages. These attacks target the infrastructure that supports blockchain operations.
Mitigation Strategies:
- Redundancy: Use redundant network infrastructure to ensure that services remain operational during an attack.
- Traffic Filtering: Implement traffic filtering and rate limiting to mitigate the impact of DDoS attacks.
- Regular Monitoring: Continuously monitor network traffic and employ intrusion detection systems to identify and respond to suspicious activity.
5. Cryptographic Weaknesses
What They Are:
Blockchain relies heavily on cryptographic algorithms to secure transactions and data. Weaknesses in cryptographic methods can compromise the security of the entire blockchain.
Mitigation Strategies:
- Strong Algorithms: Use industry-standard cryptographic algorithms and update them as newer, more secure methods become available.
- Key Management: Implement robust key management practices to protect cryptographic keys from unauthorized access.
6. Node Compromise
What They Are:
Nodes in a blockchain network can be targeted and compromised, allowing attackers to manipulate data or disrupt network operations.
Mitigation Strategies:
- Secure Configuration: Ensure that all nodes are securely configured and regularly updated to protect against vulnerabilities.
- Access Controls: Implement strong access controls and monitoring to detect and prevent unauthorized access to nodes.
7. Supply Chain Attacks
What They Are:
Supply chain attacks target the development and deployment processes of blockchain systems. Attackers may insert malicious code or vulnerabilities during the software supply chain.
Mitigation Strategies:
- Vendor Management: Vet and monitor third-party vendors and service providers carefully.
- Code Integrity: Use checksums and digital signatures to verify the integrity of software updates and code.
Conclusion
As blockchain technology evolves, so do the security threats that accompany it. By understanding and addressing these top security threats, organizations can better protect their blockchain systems and ensure their integrity. Regular audits, secure coding practices, education, and robust security measures are essential for mitigating these risks and maintaining a secure blockchain environment in 2024 and beyond.









